Defining Features of the Top-Rated KYC Providers
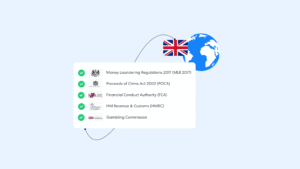
Top-rated KYC providers balances technological innovation while adhering to strict regulatory obligations. The right KYC provider can significantly influence a company's reputation, operational efficiency, and bottom line....