Advancements in fraudulent methodologies have created an urgent demand for robust Identity Verification software (IDV solutions). Fraudulent content created by Artificial Intelligence (AI), known as deepfaked content, bypasses traditional verification platforms too often. Businesses are now turning to KYC Identity Verification online to counter these emerging threats.
This guide covers all the essentials you need to know about identity verification solutions and how businesses should verify client identity online.
What Is Identity Verification (IDV)?
In simple terms, IDV is the process of the identity of new customers. The verification process may use various methods, including requesting government-issued identification or utilizing Know Your Customer (KYC) identity verification software.
IDV is paramount to achieving regulatory compliance. In the digital age, identity theft and fraud are on the rise, especially with the increase of online companies prompted by Covid-19 restrictions. In fact, up to 70% of businesses are investing more in their online presence.
A robust Identity Verification process is the best fraud detection tool, helping financial institutions and other organizations protect themselves, their customers, and their assets.
What Is Digital Identity Verification?
Digital identity verification utilizes software to confirm someone’s identity online. It is nearly always completed during the customer onboarding process and can include checking government databases, social media profiles, and other publicly available information.
KYC Vs. AML Identity Verification
KYC is the process of confirming the identity and intentions of clients in a financial context. On the other hand, AML, or Anti-Money Laundering, refers to preventing illicit funds from entering the financial system. You can read more about the topic here: KYC vs AML – What Is the Difference?

Therefore, KYC and AML identity verification processes are essential for businesses handling financial transactions.
The Types Of Identity Verification
There are various methods for confirming someone’s identity. These include:
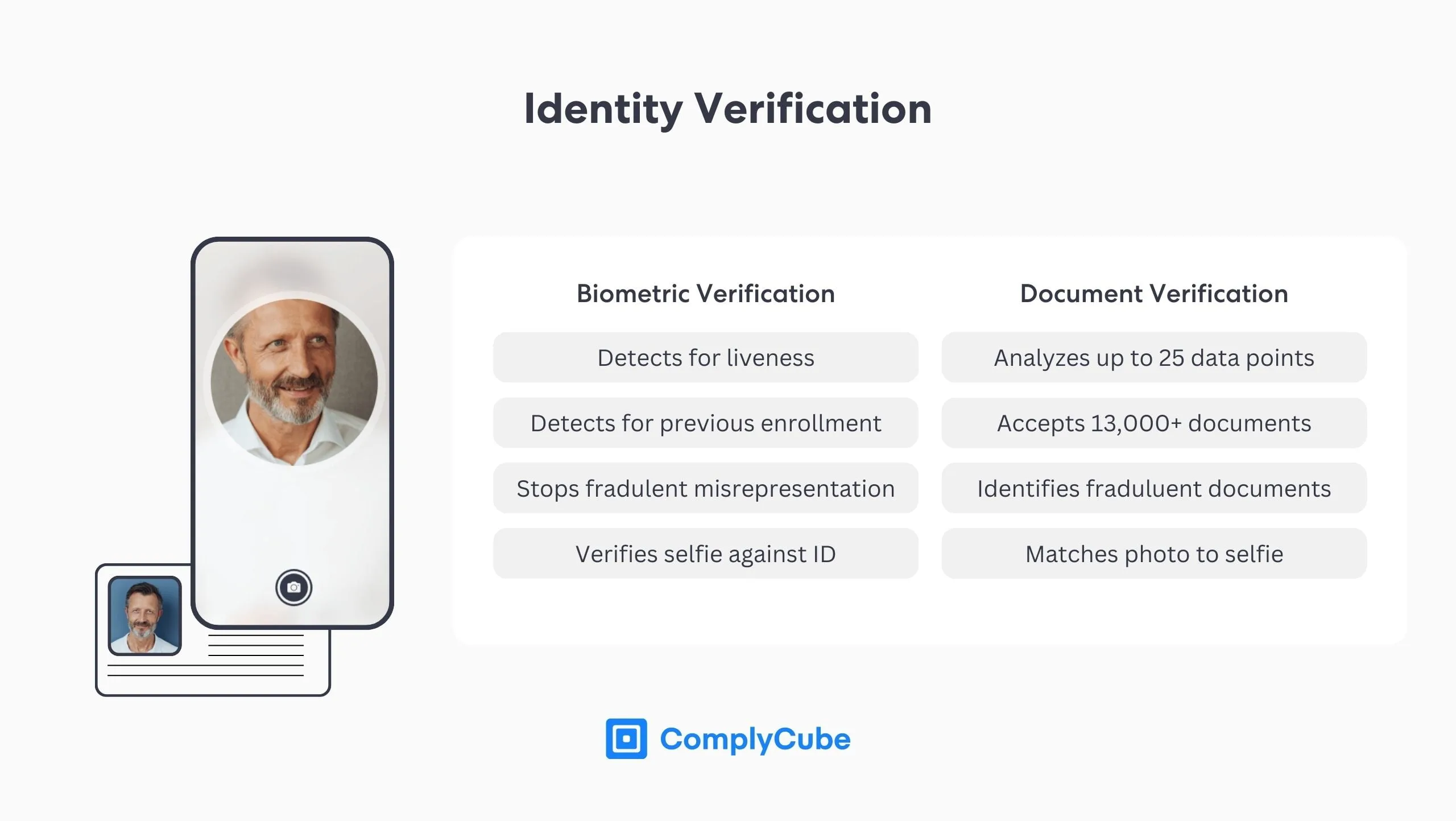
Identity Document Verification
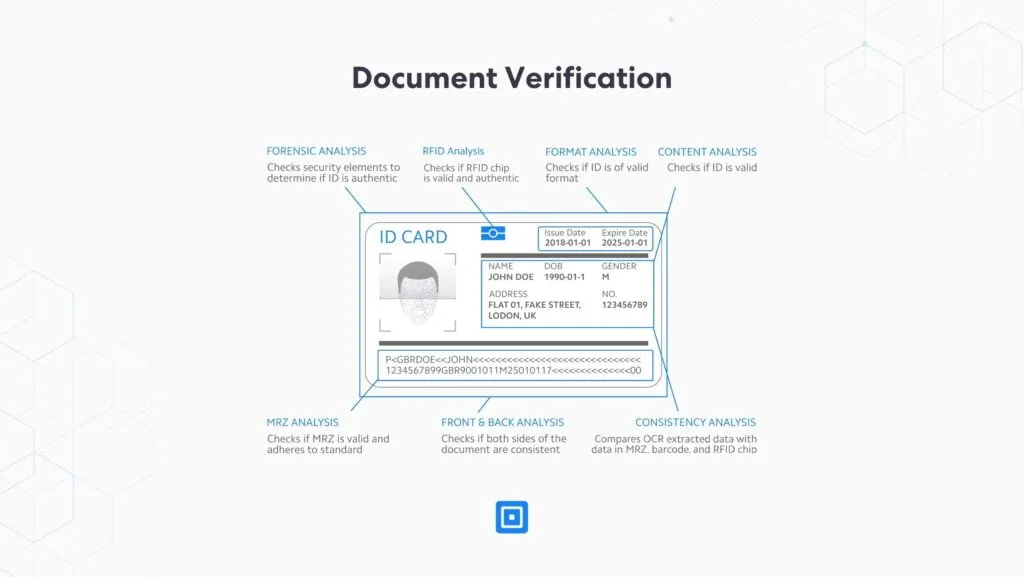
Document verification is the process of authenticating an identity document, such as a driving license or a passport, to prove it is genuine, valid, unexpired, and has not been tampered with.
The verification process involves checking documents for several features, including holograms, watermarks, stamps, encodings, fonts, and other security features. It may also entail checking whether the document has been reported lost, stolen, or never been issued. For example, Belgium’s CheckDoc service, maintained by its federal police, offers a web interface and APIs (Application Programming Interfaces) to verify the status of national IDs, passports, and residence permits.
Verification can be conducted manually by expert human reviewers or through identity verification software. Today, it’s not uncommon for businesses to prompt online users to snap their ID documents and take a selfie or short video to prove liveness when opening an account. Customers expect this process to be fast and frictionless, but this can be challenging for large institutions to deliver at scale without the right identity verification software in place.
Some of the most promising technologies that complement document verification include Near-Field Communication (NFC) verification and biometric checks, which fend off fraud by verifying that the individual seeking to use your service is genuinely behind the attempt.
Biometric Verification
Biometric verification utilizes advanced algorithms to analyze unique physical attributes (i.e., biometrics), such as fingerprints or facial traits, to confirm a person’s identity. Many enterprises use this method in conjunction with document verification to establish that the person presenting the identity document is indeed the same as the document holder.
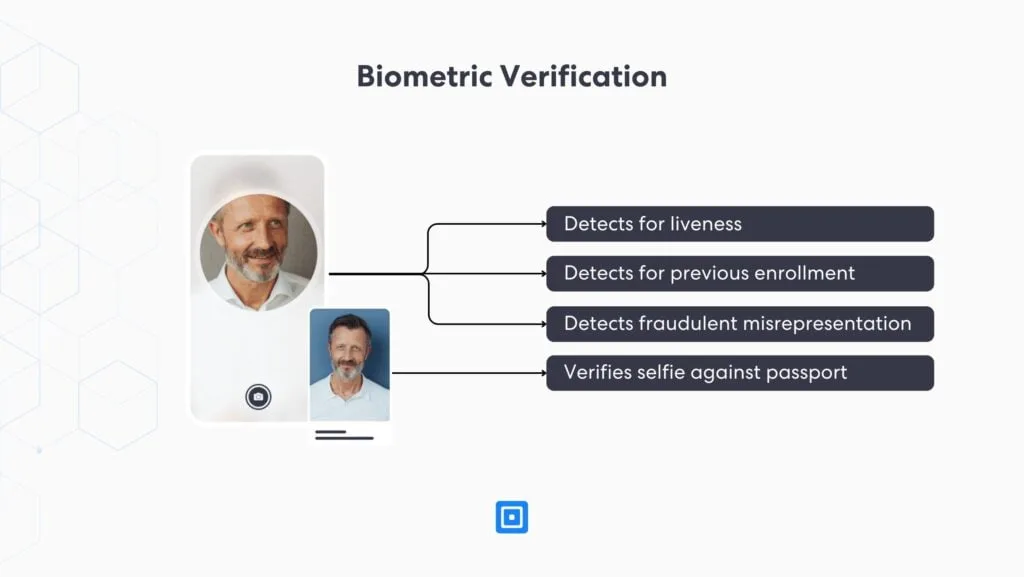
Biometric verification can also be used for authentication purposes if the collected biometrics are stored and indexed appropriately (e.g., 3D face maps). Biometric authentication has many advantages, such as improved security and convenience. You can find more information about it here: The Advantages Of Biometric Authentication.
Liveness Detection
Liveness detection is a process used to ensure that the person undergoing identity verification is present and not using a fake or manipulated photo or video. It uses advanced biometrics and image analysis, typically underpinned by Machine Learning (ML) models, to establish whether the person attempting to verify themselves is physically present and is not an inanimate object such as a 3D mask or a photo of a photo.
There are two types of liveness detection, active and passive biometric checks, which you can learn more about here: What are Active and Passive biometric checks?
Knowledge-Based Authentication (KBA)
KBA involves asking personal, knowledge-based questions to which only the genuine individual would know the answer. It can include past addresses, credit card numbers, or other personally identifiable information.
eIDV (electronic Identity Verification)
eIDV, also known as database or KYC data checks, involves corroborating personal customer information, such as name, date of birth, address, and SSN, against authoritative data sources. The sources may include consumer reporting agencies, credit bureaus, utility data (e.g., phone, electricity), and government databases. You can learn more about the various source types used in eIDV checks here: Multi-Bureau Check.
In certain jurisdictions and use cases, regulators go further by stipulating a “2+2 check”, which ensures at least 2 customer attributes have matched on 2 independent data sets.
eID (electronic identification)
An eID is a digital solution for proof of identity, typically issued by banks or government entities. It is used for authentication, login, or signing electronic documents with a digital signature. One example of eID is an electronic identification card (eIC), a physical card that can be used for online or offline identification or authentication purposes. Another form of eID is the Swedish BankID, which returns the verified name and national ID number of an end-user.
And with the prevalence of mobile phones and their relatively low cost compared to a card-based system, the eID ecosystem has seen Mobile ID gain more traction due to its convenience and security.
While these are just a few examples, there are countless ways to verify someone’s identity. Businesses can combine these methods to ensure a robust identity verification process in line with their risk-based approach.
But what are the typical components of an identity verification process? Let’s find out.
The Identity Verification Process
There are multiple steps to the verification process, namely:
- Identification: The first step in identity verification is to gather personal identification data points, such as an address, a government-issued ID, and a selfie.
- Verification: Then, you should verify the collected data using suitable identity verification software, trained KYC agents, or a combination of the two.
- Authentication: Your business can authenticate the identity through additional methods, such as biometric authentication or KBA.
- Continuous Monitoring: Even after you complete the initial authentication, the verification process doesn’t end. It’s essential to continuously monitor changes or red flags in a person’s identity or status throughout your relationship with the customer.
By following these steps and utilizing multiple verification methods, businesses can protect themselves and their customers from fraud and identity theft.
Why Do You Need Identity Verification?
So, now that you know what identity verification is, the different types, and the process, let’s discuss why you need it for your business.
Prevent Fraud
Identity verification software is there to prevent fraud. By verifying the identity of your users, you can ensure that the person is who they say they are and that they’re not using someone else’s information. Generative AI can be used to create convincing copies of KYC documents, which can easily bypass outdated AML and KYC controls.
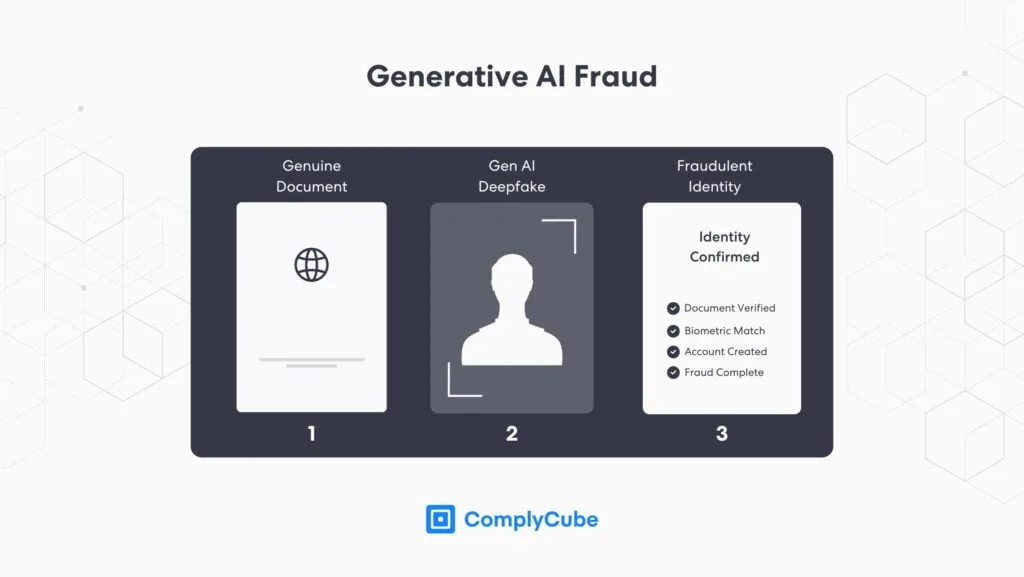
Fraud prevention is even more vital when dealing with sensitive information, such as financial data or sensitive information.
Comply With AML Regulations
It’s also crucial to comply with regulations. In many industries, some laws and regulations require businesses to verify the identity of their users.
These regulations are enforced by many different bodies, depending on your location. Here are a few major AML regulatory bodies around the world:
- Global – FATF
- UK – FCA
- Netherlands – FIU
- US – FinCEN
- Canada – FINTRAC
- China – CBIRC
- Hong Kong – HKMA
- Japan – FSA
- Singapore – MAS
- Australia – AUSTRAC
- South Africa – FICA
- UAE – NAMLCFTC
This is not an exhaustive list of bodies that mandate identity verification to fight money laundering and protect consumers from fraudsters. Often a country may have more than one regulator covering different aspects of fraud or specializing in a particular industry. Nevertheless, each has the mandate to prevent fraud and ensure that businesses within their jurisdiction adhere to the laws set out by the government.
Protect Your Data
Verifying your user’s identity can ensure that only authorized individuals can access your data. Therefore, it’s crucial for businesses dealing with sensitive customer data, such as personal or financial information.
Improve Customer Experience
In today’s online world, customer experience is everything. Customers are more likely to continue using your service when they are satisfied and safe. They are also more inclined to spread the word about your fantastic solutions.
That’s why robust identity verification is essential to keeping your customers happy. By verifying your users, you can ensure they are who they say they are and that they aren’t using someone else’s information. This can help to reduce customer frustration and increase customer satisfaction.
Battle Financial Fraud
In addition to preventing fraud in general, identity verification software can also help battle financial fraud.
By confirming the identity of a user, businesses can ensure that they are not dealing with fraudulent credit cards or bank information. It can save the company from costly chargebacks and losses due to fraudulent transactions.
Improve Trust
Overall, identity verification software improves trust between a business and its customers. By having these verification precautions in place and protecting the company’s data, you can show their customers that you take security seriously and safeguard their personal information. This can lead to improved customer relationships and trust in the business.
The Top Businesses That Need KYC Identity Verification
Now it’s time to discuss which firms and industries need KYC identity verification the most.
Banks
Banks are perhaps the most apparent business that needs to perform KYC identity verification. Customers must first provide proof of their identity to open an account, deposit or withdraw money, or apply for a loan. This helps to prevent money laundering and other financial crimes.
Cryptocurrency Exchanges and Fintechs
Crypto firms (known as Virtual Asset Service Providers, or VASPs) and Fintech companies, such as online lenders and payment apps, must also implement identity verificaation software. Over recent years, they have been the target of increased financial fraud, money laundering, and finance proliferation. These businesses often deal with sensitive financial information and need to confirm the identity of their customers to protect against fraud and comply with regulations.
Telecoms
The use of mobile devices has increased exponentially over the past few years, with mobile users crossing the 7 billion mark in 2021. Telecom airtime providers, be it Mobile Network Operators (MNOs) or Mobile Virtual Network Operators (MVNOs), typically retain personal data and conduct a credit check before granting a customer a ‘post-pay’ or ‘monthly contract’. On the other hand, pre-paid or ‘pay as you go’ SIM card holders’ identities are not actively checked. However, as of early 2021, 157 countries have mandatory SIM registration laws stipulating that customer identities must be reliably established before SIM activation.
With the onset of the COVID-19 pandemic and increasing digitalization, many Telcos are now compelled to leverage online identity verification software to save costs, reduce onboarding time, and improve the customer experience while complying with mandatory registration rules.
Video Games
The video gaming industry has been booming over the past decade, but even more so after COVID-19. With a large proportion of video games now facilitating transactions, such as purchasing new skins, mods, and in-game items, companies operating in such industries are becoming more vulnerable to identity fraud and money laundering.
Operators facilitating such transactions and content should now use identity verification software and KYC services to verify their users’ identity, age, location, and source of funds. These new practices have come into play to protect vulnerable children and keep terrorist financing and money laundering at bay.
Metaverse
With the advent of Web 3.0, several companies, including Meta and Disney, are building experiences in the Metaverse. Yet, amid hype and promise, there’s a lot to be done to make the Metaverse a safe place. However, without verified and trusted identities, anonymous bots and nefarious actors can wreak havoc in Metaverse.
Therefore, identity verification software will be vital in enabling numerous use cases for virtual worlds, including new collaborative experiences, by combining the benefits of in-person and remote communication. Identity verification will also be crucial in age verification checks and protecting the vulnerable, as avatars may change regularly, and illegal attempts are made to access restricted content, such as novel gambling experiences.
The ecosystem of the Metaverse will also undoubtedly facilitate transactions of goods and services using NFTs (Non-Fungible Tokens) or other forms of digital currency, making it vital to establish the real identities of the transacting parties.
Online Retailers
The e-commerce industry has been booming over the past few years. In 2020, the United Nations documented that the percentage of retail sales that happen online increased from 16% to 19%.
This dramatic increase has left the door open for scammers and fraudsters. The issue is that customers expect online retailers to have fast checkouts, and this makes identity verification difficult.
That’s why it’s essential for e-commerce stores to use verification that is easy-to-use, and quick to authenticate. In doing so, they can prevent credit card and identity fraud.
Government Agencies
Government agencies are also required to perform KYC identity verification. For example, citizens must first provide proof of their identity to obtain a passport, driver’s license, or other government-issued ID.
Choosing The Right Identity Verification Software
Choosing the right identity verification software for your business can be difficult. Here are some factors to consider when choosing the right software:
- Does the software meet regulatory requirements for your industry?
- Is it user-friendly for both customers and employees?
- Can it integrate with your current systems and processes?
- How secure is the software, and what measures does it have to protect customer data?
- Does the software have a good reputation and strong credibility?
Choosing a reputable and secure identity verification software that meets your business needs and industry regulations is crucial.
Don’t skimp on security — investing in proper identity verification can save your business from costly fraud and improve customer trust.
About ComplyCube’s
Identity verification is a critical step in protecting your business and customers. Verifying your customers’ identities ensures that only authorized individuals can access your products or services. There are many types of identity verification, but all of them serve a common purpose—to protect your business and customers.
If you’re looking for a reliable and affordable way to verify your customers’ identities, ComplyCube is the partner you need. Our identity verification platform is easy to use and can be customized to meet the unique needs of your business. Sign up today and see how our innovative IDV and KYC solutions can help you keep your business safe and secure.



