Impersonation fraud and account takeover attacks (ATOs) are on the rise and costing businesses billions of dollars each year. So, how do you protect your business against such attacks after the biometric verification stage? Modern biometric authentication solutions are increasingly seen as viable solutions. But what is biometric authentication?
Biometric identification is a process that uses unique physical characteristics to identify individuals. This type of authentication is far more secure than traditional methods like passwords and ID cards.
In this blog post, we’ll discuss the advantages of using biometric systems in your business. Keep reading to learn more.
What Is An Account Takeover Attack?
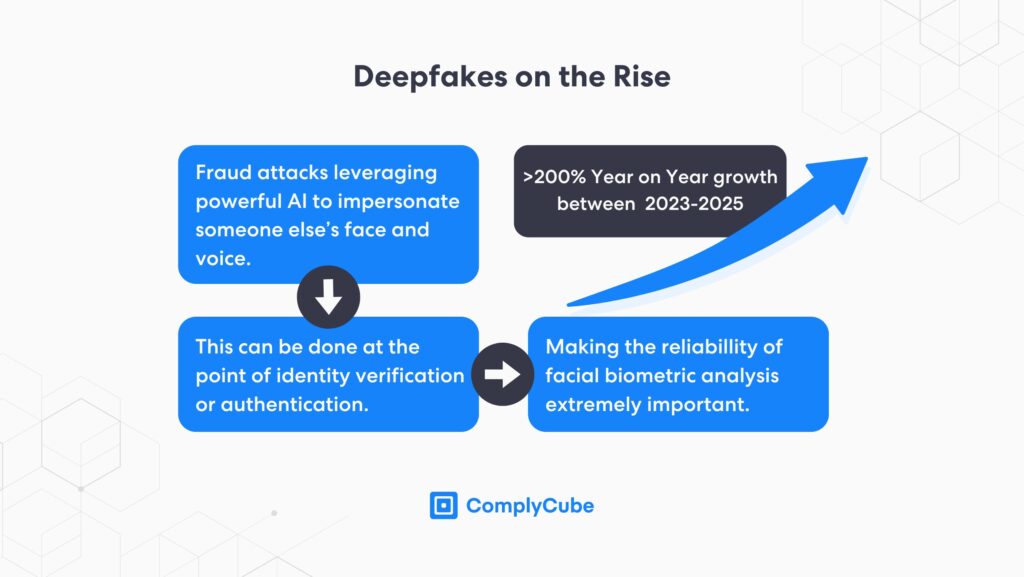
Account takeover is a form of online identity theft in which a cybercriminal gains unauthorized access to an account belonging to someone else. Criminals then exploit victims’ accounts to either hold funds or access products, services, or other valuable items such as sellable private information.
What Is Biometric Authentication?
Biometrics is the science of measuring and calculating human characteristics from physical data. Biometrics identification and access control is a type of computer security based on biometrics.
Essentially, this is a method of authenticating oneself using one’s body rather than memorizing a series of digits or phrases. Thanks to biometric solutions, governments, businesses, and other services may now safely provide access to systems with more secure authentication than ever before.
How Does Biometric Authentication Work?
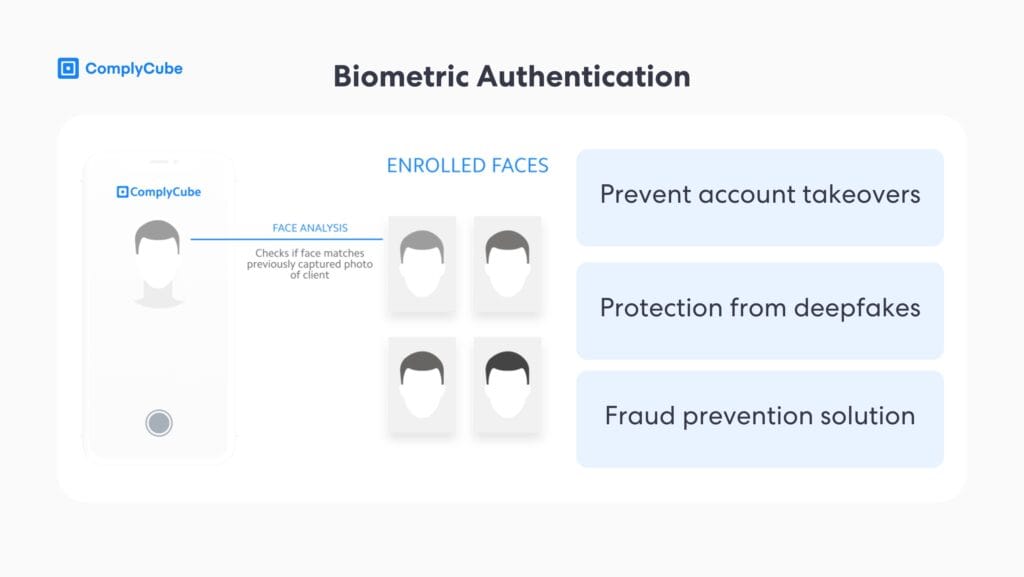
A biometric system needs specialized input devices such as fingerprint or iris scanners. However, it also works with conventional devices such as webcams or CCTVs linked with an on-premise or a cloud computer system running specialized biometric software.
These devices take measurements of your unique physical characteristics and compare them to a database of approved individuals. If there’s a match, you’re allowed access. If not, the device denies access. This process is far more secure than passwords, which can be guessed or stolen.
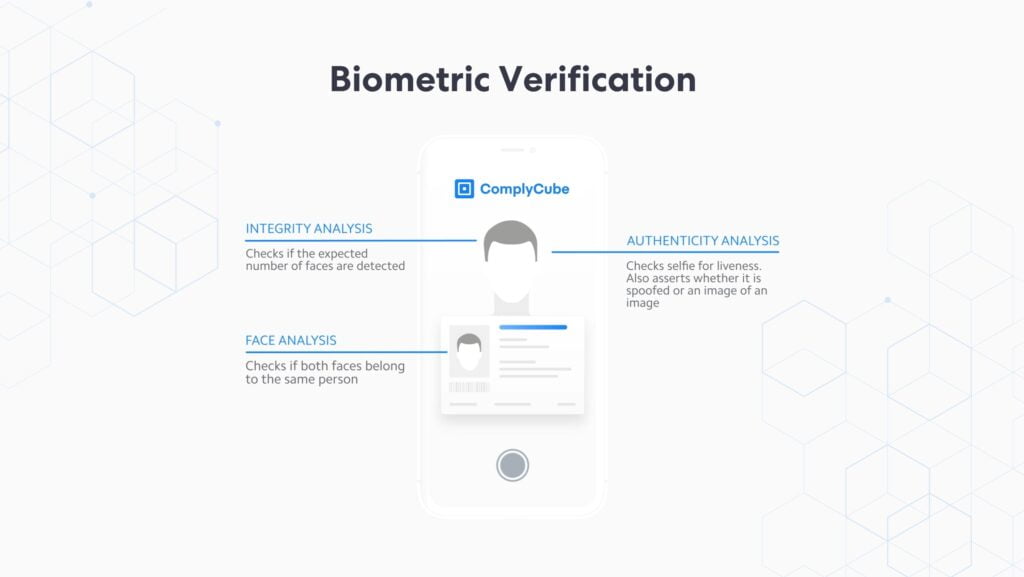
Biometric facial verification utilizes behavioral biometrics, where biometric data such as microexpressions and other mannerisms are scanned and verified. This is critical in a unimodal biometric authentication system, where only one set of data (i.e. a customer’s face) is scanned.
Sometimes, firms may choose to employ a multimodal biometric authentication system, where multiple biometric authentication methods are employed in the same verification process. Such a feature could consist of an automated fingerprint identification system coupled with a facial verification flow. However, typically firms opt for a biometric selfie verification as the preferred and most secure option.
Types Of Biometric Authentication
There are different types of biometric authentication in use today. Here are some of the most popular.
Fingerprints
Fingerprint recognition and verification used to be the most common form of biometric authentication, and it one of the most accurate forms/ Fingerprint scanners are extremely reliable and it’s extremely challenging to replicate someone else’s fingerprint.
Iris Recognition
Iris scanners are becoming more common, as they’re very accurate and difficult to fool. They work by taking a picture of the person’s iris (the colored part around the pupil) and comparing it to a database.
Facial Recognition
Facial recognition systems are another form of biometric authentication that’s the industry standard for many firms. They use algorithms to compare a person’s face to a database of images that were captured during the original biometric verification and client identification process.
Voice Recognition
Voice recognition is a form of biometric authentication that’s becoming more common. It works by analyzing the person’s voice to identify them.
Hand Geometry
This is a newer form of biometric authentication that uses the person’s hand geometry to identify them. It’s less common than other forms, but it’s starting to be used more in some applications.
In addition, there are two main types of biometric authentication systems:
- Centralized: A centralized biometric authentication system stores the biometric data of individuals in a central location. When individuals attempt to authenticate, the device compares their biometric data to the data in the central database.
- Decentralized: A decentralized biometric authentication system stores the biometric data of individuals on their own devices. When individuals attempt to verify themselves, their device compares their biometric data to its own database.
Advantages Of Biometric Authentication For Businesses
Biometric authentication has many advantages over traditional methods like passwords and IDs. Here are some of the most important benefits:
Improved Security
Biometric authentication is much more secure than older methods like passwords and IDs. This is because it’s tough to replicate someone else’s biometric data.
For example, it isn’t easy to forge someone else’s facial features. And even if someone could manage to get ahold of these things, they would need access to the person’s biometric data.
So, if a business securely stores its customers’ biometric data, it will be nearly impossible for anyone to access it.
Convenience
Biometric authentication is also much more convenient than traditional methods because you don’t need to remember a password or carry an ID card. Instead, all you need is your body.
For example, if you use fingerprint authentication to unlock your work computer, you don’t need to remember a password or PIN. Instead, you can use your finger.
This is much more convenient for businesses because customers can easily access their accounts. According to Statista, in 2021 alone, there was a global increase of 1100% for biometric authentication used by financial services.
It’s also more suitable for employees because they can verify their identity without carrying around key cards, keys, or entering a pin every few minutes when they move to a different room or their device locks.
Besides, customers and employees who can access their accounts more quickly are more likely to do so. It leads to a better job and customer experience overall.
Accuracy
Biometric authentication is also more accurate than traditional methods because there’s no chance of forgetting your password or losing your keys.
For example, if you use facial recognition to unlock your phone, you’re guaranteed to be the only one who can do so. This is because your facial features are unique to you.
Furthermore, facial recognition technology has an accuracy rate of 90% to 99.97%, depending on the clarity of the image.
It’s crucial for businesses because only authorized individuals can access customer accounts. It also ensures that employees can only access the business areas they’re supposed to.
Cost-Effective
You don’t need to invest in security infrastructures like cameras. All you need is software that can verify biometric data.
It’s vital for businesses because they can save money on security costs. Not to mention their time, which is money for most business people.
Fewer Cross-Cutting Concerns
Depending on your service provider, you can often hand over those pesky cross-cutting concerns, and forget about them altogether. These can be anything from authorization to maintenance to data validation.
When you choose the right partner, you can alleviate these troubles and leave it to the professionals. They will oftentimes manage these aspects of your business, giving you more time to focus on scaling your business or day-to-day management.
How Can You Apply It To Your Business?
Now that we’ve seen the advantages of biometric authentication, let’s see how you can use it in your business. Here are some of the more popular ways:
- Employee Access Control: Verify the identity of your employees. Ensuring that only authorized individuals access your business premises.
- Customer Authentication: Verify the identity of your customers. It gives your customers complete control over who can access their accounts.
- Time And Attendance: Track the time and attendance of your employees, which helps ensure that your employees are working their required hours. In addition, you can export this information instead of having someone input it manually. Research shows that 17% of North American & European businesses use this method.
- Prevent Fake Signups: Combat fraudsters using fake or stolen IDs by comparing new customer facial biometrics with blacklisted and previously registered individuals. ComplyCube battles this complex type of fraud using Fake Authentication.
- Meet KYC Regulatory Requirements: Comply with AML/KYC laws which require regulated businesses to uniquely and reliably identify their customers.
As you can see, there are many advantages to using biometric authentication in business. If you’re not using it already, now is the time to start. Your business will thank you for it.
However, it’s essential to see how it will benefit the people bringing in the money—your customers. So, let’s take a look at that next.
How Biometric Verification Benefits Your Customers
Not only does biometric verification benefit your business and reduce the cost base, but it also achieves a great User Experience (UX) and convenience factor for your customers.
The most significant advantage customers gain from a biometric authentication business is security. It protects them from cyber-attacks, identity theft, and getting locked out of their own accounts.
Look at it like this; there aren’t cards, patterns, pins, or keys involved in the process. So, customers aren’t able to lose their access without losing their biometric identifiers. Furthermore, they can access their accounts wherever they are, as long as they have their trusted device nearby. An example of such a device is your mobile phone, and leaving the house without it nowadays is like leaving a part of yourself behind.
Biometric verification is also fast. Traditional methods like keycards can take time to swipe or insert. With biometric authentication, you simply unlock doors without fumbling around for your keys.
Potential Security Risks Associated With Biometric Authentication
While biometric authentication offers several advantages, there are also some potential security risks to be aware of. Here are three potential security risks associated with biometric authentication:
- False Positives: In some cases, biometric authentication systems may allow access to someone who shouldn’t have it. It is known as a false positive and may occur due to multiple factors, such as poor quality sensors or incorrect data.
- False Negatives: Another potential security risk is known as a false negative. It occurs when a device denies an authorized person access because the biometric authentication system doesn’t recognize their biometrics. The main factors contributing to this are dirt or oil on the sensor.
- Spoofing: Spoofing is one of the most common security risks associated with biometric authentication. It’s when someone uses a fake fingerprint to try and gain access to a system. Spoofing can be challenging to detect and used to access sensitive information.
Biometric authentication is a convenient and secure way to protect your belongings. However, there are some potential security risks to be aware of. Although, you can easily avoid these risks by setting up 2-step verification, keeping equipment clean, and choosing your biometric authentication provider carefully.
2-Step Verification And Biometric Authentication
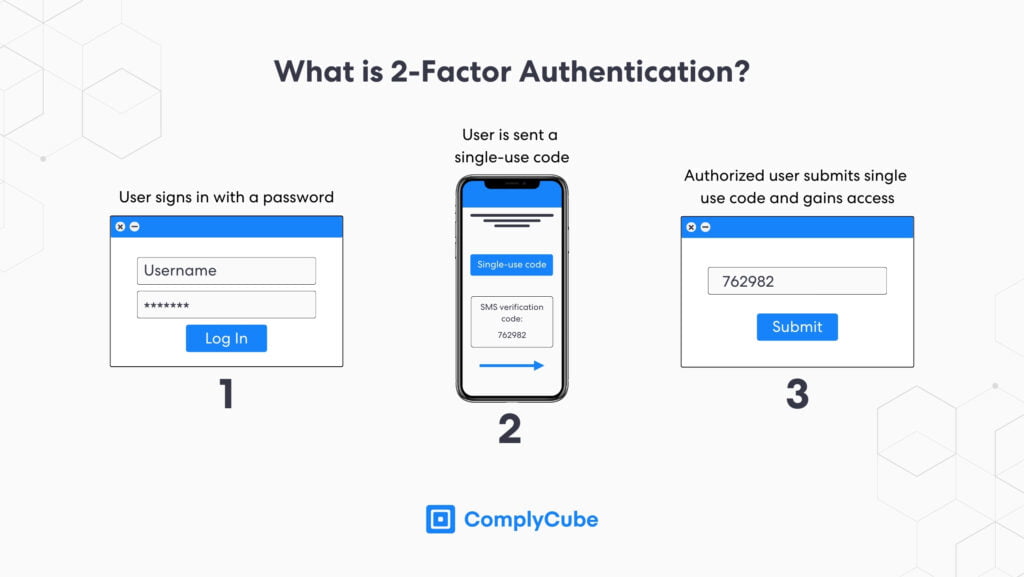
Another excellent way to ensure your device is protected is through 2-step verification alongside your biometric authentication.
2-step verification is an additional security method that requires you to enter a code and your biometrics to gain access to your information. It makes it much more difficult for someone to gain access to your accounts, devices, or anything else you want to secure, even if they have your fingerprint. Even Google uses 2-step authentication to ensure its users are protected. Typically this is an email or SMS verification workflow, but it could be a secondary biometric verification step.
Choosing The Right Biometric Verification Service
Knowing biometric authentication’s advantages and potential risks, you must choose the exemplary service. Here are five things to look for when choosing a biometric authentication service:
- Accuracy: The first thing you should look for in a biometric authentication service is accuracy. You want to make sure that the system can correctly identify authorized users. Look for services that have a high success rate and low error rate.
- Ease Of Use: You don’t want to choose a service that’s difficult to use. Look for software that offers an easy-to-use interface, integrates well, and has a simple setup process.
- Security: You want to ensure that your data is safe and secure. Look for solutions that offer encryption and other security features. It needs to protect you from fraudsters, spoofing, and tampering.
- Reach: You want to ensure the service is available where you need it. Look for a service that offers global coverage and is compatible with your devices.
- Customizability: The last thing to look for is customizability. You want to be able to customize the service to meet your needs. Look for a service that offers a variety of options and allows you to tailor the service to your specific requirements.
If your potential biometric authentication provider ticks all of these boxes, there’s no need to fear. You can rest assured knowing that your data is safe and secure.
Don’t Lose Yourself: what is biometric authentication?
Simply put, it verifies a person’s identity using physical or behavioral characteristics. In other words, it’s an incredibly secure way to ensure that you are who you say you are, no matter where you are or what device you are using.
And for businesses, that means increased security and peace of mind. But biometric authentication isn’t just about security. It also offers enormous benefits for your customers. You can improve customer loyalty and satisfaction by providing a more convenient and secure way to access your products and services.
Ready to get started? Reach out to ComplyCube today and never be concerned about your data again. You can also find more information about protecting your data on the rest of our blog.