From opening a bank account to signing up for a new service, user identity verification has become a cornerstone of secure customer onboarding in today’s digital landscape. Moreover, it ensures only legitimate users can access services, keeping fraudsters and bad actors at bay.
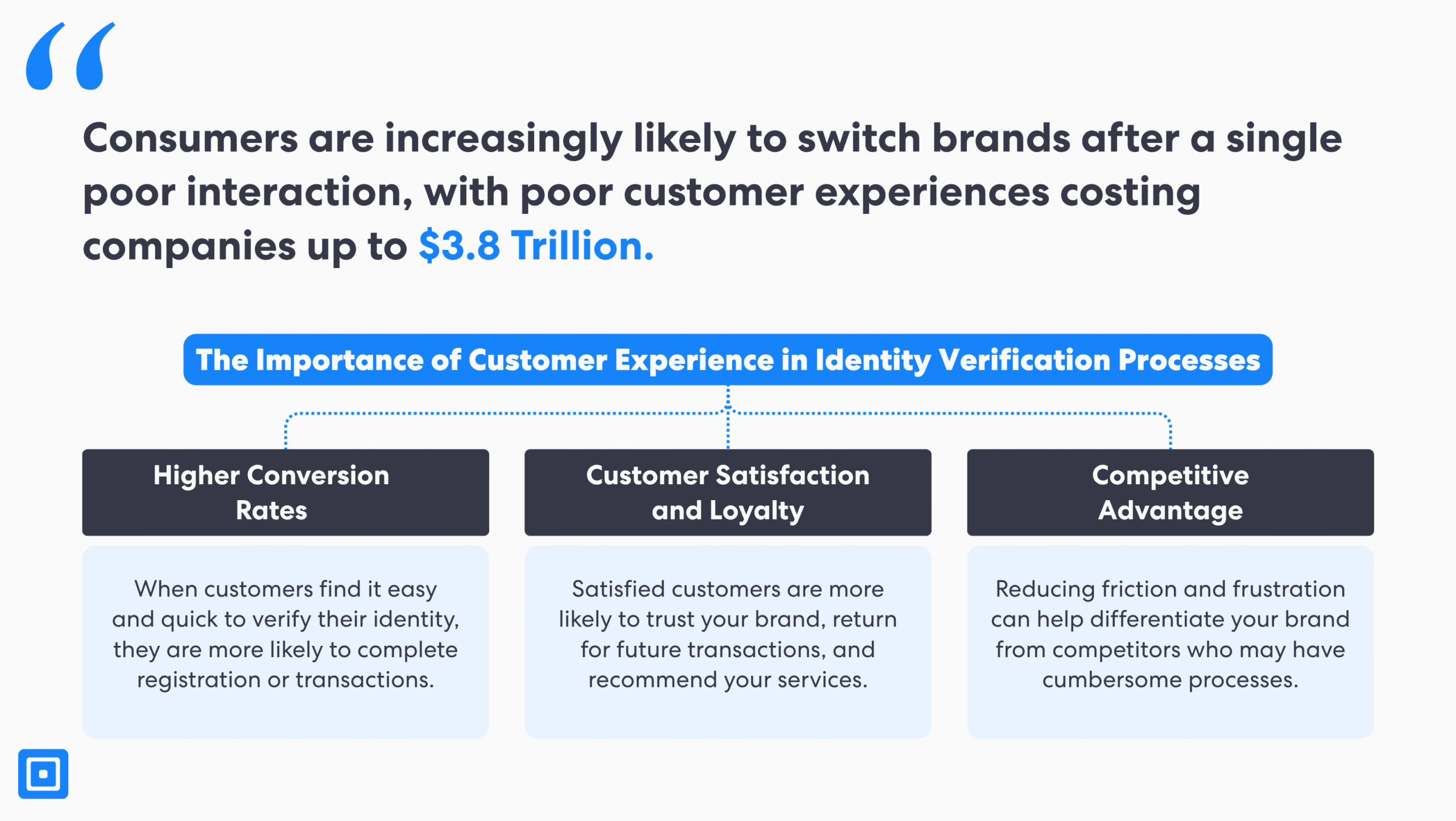
At the beginning of 2024, over £570 million was stolen from fraudulent activities as bad actors target innocent people.
The best way to protect your business against fraud is to prevent it from happening in the first place. Online identity verification emerges as a powerful tool for fraud prevention, anti-money laundering, and building customer trust.
The Function of User Identity Verification
Your user identity is the totality of important characteristics, such as your name, date of birth, official government-issued IDs, and even your biometric data. These characteristics create your unique identity, which is used in Identity Verification (IDV) to confirm that you are who you claim to be. Digital identity verification enables businesses to verify someone’s identity and design a secure ecosystem for their users and clients. It empowers them to serve legitimate, successfully verified customers while preventing illicit transactions and identity fraud.
What Does Identity Verification Involve?
The identity verification process entails various steps. Today, businesses leverage the latest technology, such as biometric and vision authentication capabilities, to further enhance customer onboarding and fraud protection efforts.
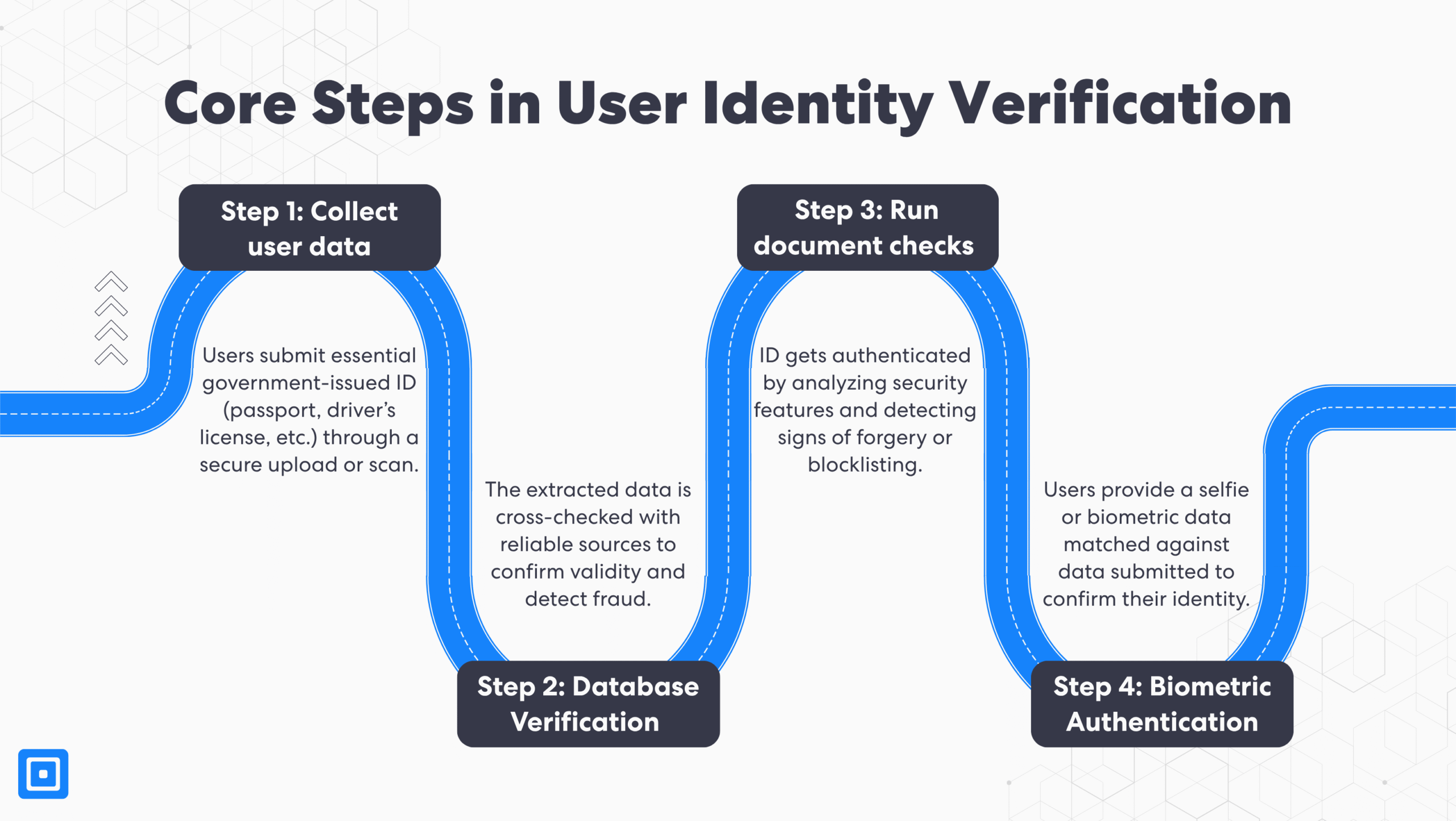
Typically, the steps involved in identity verification are:
- Collection of User Data: Organizations gather user data using various ID types, depending on the regulations and territory in which they operate. Common government ID types are passports, driver’s licenses, and unique identifiers such as Social Security numbers.
- Database Verification: The information provided will be cross-referenced against reputable sources, including credit bureaus, government data sources, utility authorities, and commercial databases.
- Document Authentication Checks: The documents uploaded will be verified and classified as either legitimate or whether they have been compromised, forged, copied from the Internet, expired, or even blocklisted.
- Biometric Verification: This step involves facial recognition technology or biometric information to match the user’s unique physical characteristics against the ID submitted, ensuring the person is who they claim to be.
Evolution of Digital Identity Verification Methods
Identity verification methods have gone beyond simple checks. Organizations are adding extra layers of security to their identity verification processes to make it harder for data breaches. Here are some of the common methods on the rise:
Answer Security Questions
Users provide personal answers to security questions, which are unique identifiers for the person’s identity. The questions include “What is the name of your first pet?” or “What is your mother’s maiden name?” especially during password recovery or as an extra authentication step.
Sending Verification Codes
Sending a one-time verification code to the user’s phone via SMS or email helps confirm the user’s identity and prevents unauthorized access. This method ensures that only legitimate account owners can complete login or registration, reducing the risk of fraud. Popular platforms such as WhatsApp and Facebook require users to enter a code on their phone to create a new account or complete the login process.
Multi-Factor (MFA) or Two-Factor Authentication (2FA):
Organizations, especially banks, often combine two or more security methods as an additional layer. This method is called two-factor or multi-factor authentication. A common example is requesting a password, plus a verification code sent to the authenticator app, or even biometric information.
Advanced Biometric Authentication:
Liveness detection, including face depth analysis, micro-expression detection, and occlusion recognition, safeguards businesses from sophisticated deepfakes. Additionally, fingerprint scanning and voice recognition are used increasingly to verify a user.
Establishing User Transparency and Trust
Managing identity verification and privacy can be complex. Safeguarding user privacy is the key to cultivating brand trust and compliance with regulators. Identity verification solutions and vendors need to be transparent about:
- Data Collection: For what reason is data gathered, and what specific information is collected?
- Data Storage: Where will the data be stored? How is the data being stored securely, and for what duration?
- Data Protection: What types of security measures or technologies are used to align with privacy laws?
- User Consent: Does the customer have the right to access or delete their data?

Complying with local and global regulations is critical. For example, the GDPR mandates explicit consent and strong data protection for EU and UK users.
Prioritizing Seamless Customer Onboarding in Identity Verification Methods
Integrating a smooth user onboarding journey is beneficial in increasing conversion rates. Requesting too many documents or unnecessary steps can be frustrating and lead to a high user drop-off rate. In contrast, lax identity verification methods will invite more fraudsters.
Here are the best practices for building a strong onboarding process:
- Clear Step-by-step Instructions: Use visual icons, accessible interfaces, and clear and concise text to walk users through the process.
- Provide Feedback: When necessary, provide feedback when a user fails verification. Additionally, providing more than one attempt for a user to verify their identity can be helpful, especially with real-time verification methods that can be affected by a poor wifi connection.
- Guidelines and Privacy Statements: Include guidelines, such as examples of a good document submission versus a poor one. For privacy statements, clearly explain how data is collected and processed.
- Inclusion with Multiple ID Types: Be mindful of what ID types your organization accepts. Allowing users to choose and submit various identification documents helps accommodate different user needs and minimizes friction.
- Automated Tools and Integrations: Businesses increasingly use Artificial Intelligence (AI) and other integration tools, such as an extraction feature, to handle routine checks and make ID verification significantly faster and more secure.
Implementing these best practices will ensure organizations maintain high security, prevent fraud, and mitigate social engineering attacks, while building a positive customer experience.
Emerging Trends in Identity Verification Software
Modern IDV software leverages state-of-the-art technology, including AI, Machine Learning (ML), Blockchain, access control systems, and more. Businesses can deliver quicker services to their customers while addressing stringent regulatory compliance. The top trends you can find in ID verification processes are:
Ongoing Monitoring: Advanced identity verification software has ongoing monitoring capabilities beyond the initial ID verification. This means a customer’s transactions and online activity are continuously tracked in real-time. Any suspicious activity that arises will be flagged immediately, enhancing the fraud prevention and anti-money laundering efforts.
AI-Driven Checks: AI and Machine Learning (ML) support identity verification processes by analyzing government-issued IDs, scanning for synthetic identities, and enhancing biometric authentication in seconds. Adopting AI technologies is a critical step in verifying someone’s identity and enhancing security quickly, delivering long-term cost savings.
Decentralized Identity Solutions: Users choose and control their own identity information, typically with blockchain technology. Sensitive data is managed by the users instead of being stored in central databases. This gives them more privacy, reducing the risk of data breaches.
Digital Identity Wallets: These refer to apps or services where users can store their electronic documents. They enable users to easily share their identity when it’s required, making the customer verification process quicker and safer.
No-Code and Low-Code Identity Verification Solutions: Identity verification solutions enable compliance teams to design tailored customer verification processes without programming knowledge. Companies can expect more straightforward and flexible set-up workflows, empowering them to make informed decisions while meeting regulatory requirements.
Build Seamless Customer Onboarding with Cutting-Edge User Identity Verification Solutions
By using advanced technologies and security features such as two-factor authentication and monitoring users’ behaviour, companies can proactively prevent fraud and build a secure system for customers. Adopting strong, user-friendly identity verification tools into your onboarding process not only protects accounts and sensitive data, but also builds trust, increases conversion rates, and ensures your business meets evolving compliance standards.
Unlock seamless customer onboarding by implementing a secure and efficient identity verification process that balances enhanced security with a smooth customer experience today. Speak to a member of the team.