TL;DR: A biometrics identity verification system helps verify users, but the best biometric identity verification solutions catch spoofing attempts and manipulation in real time. With biometrics-based identity verification, businesses can reduce fraud, protect their businesses and stay compliant.
What is a Biometrics Identity Verification System?
A biometrics identity verification system is a digital tool that verifies a person’s identity. They verify a person’s identity by analyzing their physical features, such as facial geometry or voice patterns. This ensures that the biometric verification process works and that each identity is tied to something a person inherently is, rather than something they know or have.
Biometrics identity verification systems use distinct physiological and behavioral characteristics to authenticate individuals securely and accurately. This can include fingerprints, facial features, iris patterns, voice and more. These identifiers are extremely difficult to replicate, making biometrics one of the most reliable methods for digital verification.
How Do Biometrics Identity Verification Systems Work?
The best biometric identity verification process is necessary for confirming that the person submitting identity documents is the actual owner. Unlike traditional methods such as passwords or PINs, biometrics-based identity verification uses traits that are unique to each person. These verification metrics make it extremely difficult to forge or replicate. This approach enables the system to verify and identify individuals based on their unique traits.
Typically, a biometrics identity verification system captures a live image of the user’s face through a webcam or smartphone camera. It then, compares it to the facial image on an official document such as a passport or driver’s license. This comparison helps determine if the two images belong to the same person’s identity. This makes biometric systems a cornerstone of secure digital identity verification.
Types of Biometrics Identity Verification Systems
Biometric authentication leverages a variety of technologies. Foregoing traditional methods to authenticate users, they make use of advanced biometrics-based identity verification. These biometric systems are based on their unique biological and behavioral characteristics.
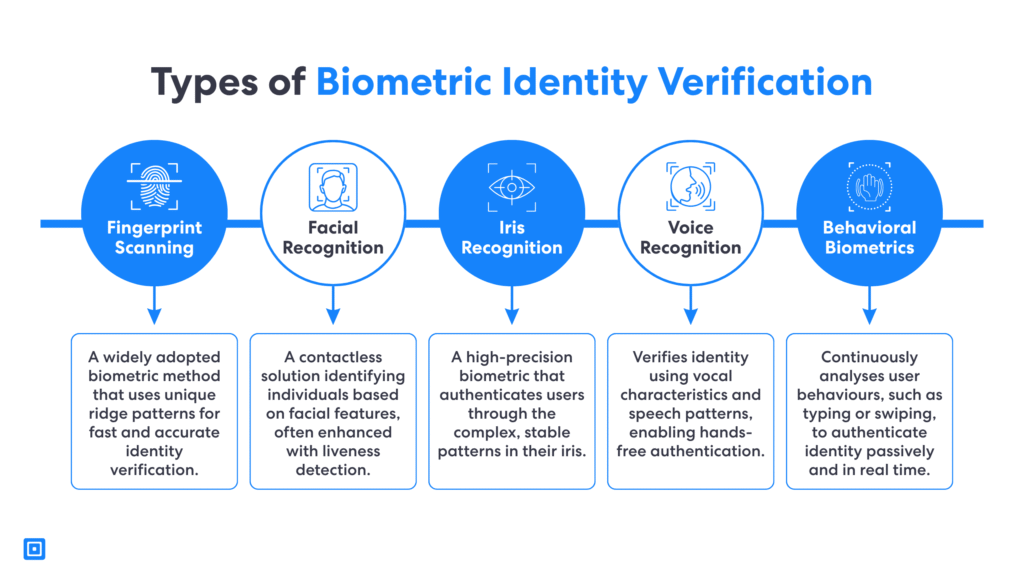
Fingerprint Recognition
One type of biometrics-based identity verification is fingerprint recognition or fingerprint scanning. This type analyzes the distinct patterns and ridges found on an individual’s fingertips to verify identities. A fingerprint scanner approach is most commonly used. This approach is used in mobile devices, access control systems, and prevent unauthorized access to secure facilities.
Facial Recognition
Another example of biometrics-based identity verification is facial recognition. Widely adopted in consumer electronics, it ranks among the top biometric identity verification methods. By utilizing sophisticated algorithms to map and compare facial features. This technology streamlines the authentication process and also incorporates liveness detection. This helps to guard against increasingly sophisticated identity fraud and spoofing attacks.
Iris Recognition
Iris recognition is also one of the best biometric identity verification methods. Renowned for its precision, iris recognition requires a scan of the intricate patterns in the colored part of the eye. This biometrics-based identity verification offers an secure solution for environments requiring the highest level of protection.
Voice Recognition
Then, voice recognition adds another layer of security by analyzing the unique patterns in a person’s speech, such as pitch, tone, and cadence. This type of biometrics-based identity verification makes it ideal for hands-free authentication and remote verification scenarios.
Behavioral Biometrics
Finally, behavioral biometrics focus on identifying users through their behavioral characteristics. Unlike fingerprint recognition, facial recognition, or voice recognition, it takes into account things such as typing speed, mouse movements, or gait recognition. This provides continuous authentication and further reducing the risk of impersonation.
While every one of these biometric verification methods enhances security, they rely on unique patterns that are extremely difficult to replicate. For example, this helps organizations with problems such as authenticating users for online banking, or preventing identity fraud with mobile banking and financial transactions. Biometrics-based identity verification ensures that only authorized personnel gain access to sensitive information, and are most effective when layered alongside one another.
Facial Recognition Technology in a Biometrics Identity Verification System
Facial recognition technology is the core mechanism behind most of the best biometric identity verification systems. This technology scans a user’s live facial image and compares it to their submitted identity document. By using sophisticated algorithms to assess hundreds of facial data points, including eye position, jawline structure, and skin texture, these measurements are converted into a unique facial map.
A facial recognition map uses a specific system to calculate a match score. This biometrics-based identity verification system matches the live map to a stored template or stored data for verification. This mapping of the biometric selfie to the image on the identity document is known as a Face Match, and ensures that the photo on the ID and the selfie belong to the same person.
What sets the best biometric identity verification systems apart is their ability to account for variations. Users may take selfies in different lighting, at various angles, or with slight changes in appearance such as facial hair or aging. Effective systems are trained on diverse datasets and use AI models that adapt to these conditions, ensuring accurate verification across different ethnicities, ages, and environments.
Liveness Detection
Liveness detection ensures that the person presenting their face is physically present and not attempting to trick the system using a static image or digital manipulation. Moreover, it plays a critical role in defending against impersonation tactics for processes such as patient identification or mobile banking.
Nevertheless, liveness detection is a critical step within the broader biometric verification process. Liveness detection works alongside other stages such as capturing, analyzing, and validating biometric data to ensure security, accuracy, and user convenience. In addition, without liveness detection, even the best biometric identity verification and face match systems are vulnerable to attackers using realistic decoys to gain access to accounts or services.
Passive vs Active Liveness Detection
There are two main categories of liveness detection in biometrics identity verification systems: active and passive. Active methods prompt users to perform an action. Passive detection, by contrast, operates silently in the background and evaluates indicators to determine if the face is real.
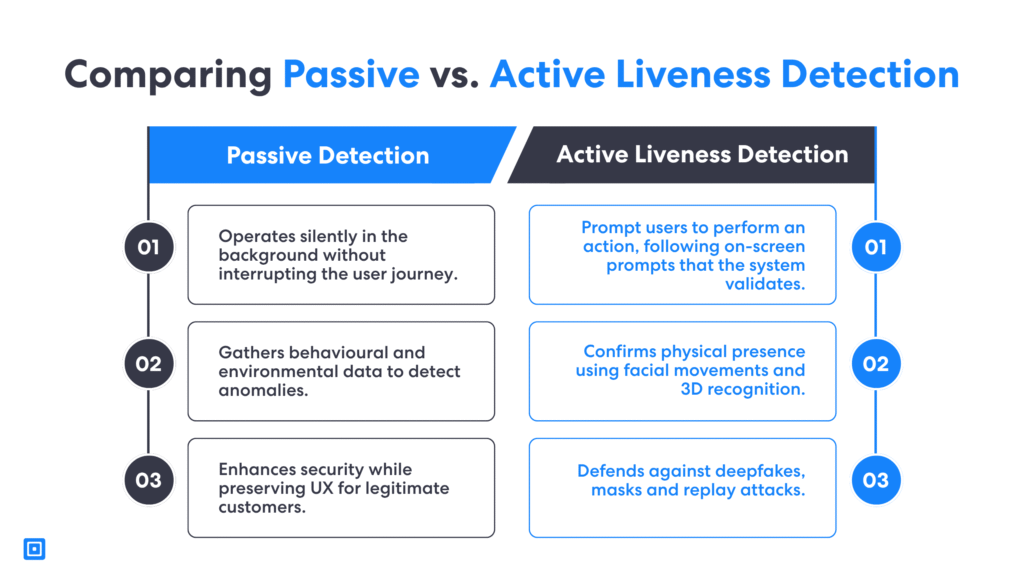
Active liveness detection methods are effective in high-security scenarios where maximum assurance is needed. First, they require the user to follow on-screen prompts, such as looking left or smiling. This then validates in the system as proof of life. While this approach offers a strong defence against spoofing, it introduces user friction and can disrupt the customer journey, especially on mobile or in low-bandwidth environments.
On the other hand, passive liveness detection works automatically during the face capture process. Using subtle clues such as depth perception, skin sheen, and light reflection, they can detect whether the face in front of the camera belongs to a real person. This is particularly useful for customer onboarding in industries such as banking or telecommunications. Passive liveness detection methods provides a smooth user experience while delivering strong fraud prevention.
Accuracy Benchmarks for Biometrics Identity Verification System
There are two metrics that come into play when trying to identify the best biometric identity verification solutions on the market. Regulators look at False Acceptance Rate (FAR) and False Rejection Rate (FRR). This ensures that systems do not wrongly approve imposters or legitimate users are not turned away.
These two factors in biometrics-based identity verification make it more difficult for unauthorized users to get access. Also, leading biometric-based identity verification provides both security and usability. For example, they often aim for 99.9% face match accuracy, providing high assurance in identity verification.
Addressing False Rejections and Bias
Biometrics-based identity verification platforms that do not mitigate against bias or address image quality may falsely reject users as part of the verification flow. In addition, some legitimate users might get denied access causing frustration and damaging trust. Biased training data, poor image qualities, or strict thresholds within biometrics-based identity verification systems can cause these errors. In order to mitigate this, biometric systems must be tested on diverse datasets.
The best biometric identity verification systems try to ensure that all processes work fairly for all users. Therefore, it is essential to conduct regular bias audits, demographic evaluations and provide regular re-training. It is also the responsibility of the developers to tune confidence thresholds and fallback processes.
Spoofing and Deepfake Threats with Biometrics Identity Verification Systems
In today’s world, biometric spoofing is becoming a significant security threat for even the best biometric identity verification systems. Fraudsters attempt to bypass identity checks using printed photos, high-resolution screens, or hyper-realistic silicone masks to gain unauthorized access. Deepfake technology can fabricate a moving, speaking face that mimics another person, posing an even greater challenge to verification systems.
To counter these threats and protect sensitive information, biometric-based identity systems incorporate multiple anti-spoofing layers. By including texture analysis, movement tracking, and 3D depth sensing, systems can detect anomalies typical of deepfakes and synthetic presentations.
These biometric system measures are essential for bolstering security against sophisticated attacks. By confirming the identity and liveliness of the subject, it makes it exceedingly difficult for attackers to deceive the system using fake media.
Case Study: GRVT Scaling Biometric Onboarding for Millions in Crypto
Problem
In 2025, GRVT, a hybrid derivatives exchange, faced the challenge of onboarding a large volume of users (over 2.5 million pre‑launch) and meeting rigorous KYC/AML standards. Deepfake attacks and identity spoofing in crypto had jumped in recent years, posing a threat to platform security and brand credibility. Without a scalable biometric identity verification system, GRVT risked delays, regulatory knock‑backs and user‑experience bottlenecks.
Solution
GRVT partnered with ComplyCube to deploy a biometric identity verification system that enabled face‑matching, document verification and liveness detection in under 25 seconds. The platform layered in global identity coverage (220+ jurisdictions), real‑time screening, and anti‑spoofing checks to confidently verify users. Integration with GRVT’s onboarding flow ensured zero downtime, high scalability, and regulatory alignment across jurisdictions.
Outcome
- GRVT achieved user onboarding in under 1 minute, significantly accelerating volume growth.
- ComplyCube’s biometrics-based identity verification system enabled GRVT to demonstrate compliance with global crypto KYC and AML standards, reinforcing trust with regulators and institutional users.
- GRVT secured a cost‑effective global verification model, processing large scale user identity checks while maintaining high assurance and low latency.
Artificial Intelligence in Biometrics Identity Verification System
Artificial Intelligence (AI) drives the accuracy and adaptability of face matching technology. The best biometric identity verification systems rely on AI to recognise subtle facial patterns and adjust to diverse real-world conditions. As technology advances, the goal is to continuously improve biometric verification.
Advancements in AI have transformed biometric identity verification from a static, one-time check into a dynamic, real-time defence system.
Chief Product Officer of ComplyCube, Harry Varatharasan remarks that “Advancements in AI have transformed biometric identity verification from a static, one-time check into a dynamic, real-time defence system. Today’s intelligent systems can detect spoofing attempts, synthetic media, and deepfakes with remarkable accuracy, while adapting continuously to evolving fraud tactics.”
In fact, these systems evolve through continuous learning, improving their ability to distinguish genuine users from fraudulent attempts. Importantly, AI-based models can also be optimised to detect demographic biases, ensuring fair and inclusive verification across different ethnicities and age groups.
How to Identify & Implement the Best Biometrics Identity Verification System
Successfully implementing the best biometric identity verification system requires a strategic approach. This approach needs to balance security, usability, and compliance. Security level, user experience, regulatory compliance, system integration, data protection and ongoing maintenance need to be considered as key criteria in selecting the right verification process.
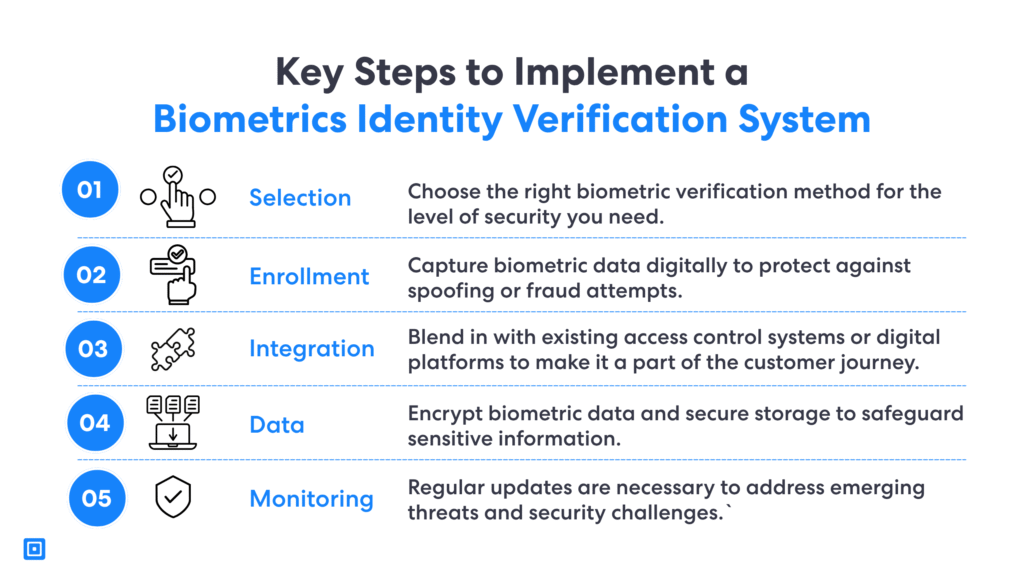
The first step is to select the appropriate biometric verification method, whether it be fingerprint recognition, facial recognition, iris scans, or behavioral biometrics. Determining the appropriate biometric verification depends on specific needs as well as level of security required. Other factors include user convenience and any relevant regulatory requirements.
Once the optimal biometric technology is chosen, the enrollment process begins. Here, users’ biometric data is captured and converted into a digital template, ensuring high-quality data collection and protection against spoofing attempts. Secure storage and encryption of biometric data are crucial to safeguard sensitive information and maintain user trust.
Finally, integration with existing access control systems or digital platforms is the next critical phase. Seamless integration ensures that biometrics-based identity verification becomes a natural part of the user journey, whether for secure access to physical locations or digital services. Continuous monitoring and regular updates are vital to address emerging threats and adapt to evolving security challenges, helping to prevent data breaches and unauthorized access.
In the implementation, companies should prioritize providing high quality service and customer satisfaction. It is crucial to have a user-friendly experience. By clearly communicating about data usage, and providing responsive support, organisations can build user confidence in the biometric verification system.
Biometrics Identity Verification System for Digital Onboarding
Global regulatory bodies have increasingly recognised biometrics as a reliable means of meeting identity verification requirements. Standards set by the Financial Action Task Force (FATF), European Banking Authority (EBA), and other regional regulators include liveness detection and biometric verification as recommended controls for onboarding and customer due diligence. You can learn more here: The Identity Verification Onboarding Bottleneck
These systems play a vital role in supporting compliance with Anti-Money Laundering (AML) and Know Your Customer (KYC) regulations. They provide a high level of assurance that helps financial institutions and digital service providers validate customer identities quickly and securely.
In addition, multi-factor authentication and multi-factor authentication systems are often recommended by regulators to further strengthen identity verification, as they integrate biometric modalities such as voice recognition and other advanced techniques. As fraud tactics evolve, regulators continue to promote the adoption of best biometric identity verification tools for identity assurance.
Enhancing Security for Biometrics Identity Verification System
Processing biometric data involves heightened responsibilities under data protection laws. Regulations such as the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) classify biometric identifiers as sensitive personal data, requiring organisations to implement rigorous safeguards. Nevertheless, biometric information, such as fingerprints or facial images, is subject to strict privacy regulations to protect individuals’ identities and prevent identity theft.
Therefore, explicit user consent is essential before collecting or using biometric data. Transparency is key as users must understand how their data or identity documents will be used, stored, and deleted. Organizations must adopt privacy-by-design principles, including secure data storage, access controls, and policies for user data deletion. These practices build trust and ensure compliance with evolving legal frameworks.
Key Takeaways about Biometrics Identity Verification System
- The best biometric identity verification strengthens identity assurance with facial images and ID documents.
- Liveness detection is critical for fraud prevention, blocking deepfakes, photo attacks, and digital injection attempts.
- Accuracy and fairness depend on smart AI, achieving 99.9% match rates while reducing false rejections.
- Regulatory compliance requires privacy-by-design in alignment with laws such as GDPR and CCPA.
- Platforms such as ComplyCube deliver real-time biometric onboarding, combining face match, spoof detection, and global coverage to reduce fraud and improve customer experience at scale.
Building Trust with Biometrics Identity Verification System
To sum up, biometrics-based identity verification has emerged as a cornerstone of digital identity assurance. By combining face match accuracy with real-time liveness detection, organisations can onboard users quickly, securely, and in full compliance with global regulations. Ultimately, the best biometric identity verification can offer superior fraud protection, faster onboarding, and a smoother user experience than traditional verification methods.
ComplyCube enables these capabilities through a unified, API-first platform offering advanced face match, passive and active liveness detection, and global document compatibility. Backed by ISO, GDPR, and eIDAS certifications, ComplyCube supports businesses in building trusted, secure customer relationships at scale.
Frequently Asked Questions
What is a biometrics identity verification system?
Biometric identity verification uses a variety of recognition technology to confirm that a person’s physical traits, typically their face, match a government issued ID document. By combining AI-driven face matching with liveness detection, the authentication process ensures the use is physically present and not using a spoofed image or video. This enhances security and maintains secure access and less security breaches for many institutions.
How accurate is biometric face match verification?
Modern biometric verification systems such as those used by regulated Regtech providers, deliver facial recognition match accuracy rates exceeding 99.9%. Advanced algorithms maintain high performance across various conditions, facial angles, and device types to keep false acceptance and false rejections extremely low. Once the biometrics obtained go through the authentication process, accuracy is further enhanced when paired with real-time document verification.
What is liveness detection in biometrics?
Liveness detection is a enhanced security feature that prevents identity theft. It determines through various methods such as iris recognition, facial recognition, voice recognition, fingerprint scanner or more, that the person undergoing biometric verification is physically alive and present during the process. It blocks any attempts to fool biometric authentication using photos, deepfakes impersonating a person’s biometrics, or replayed videos. Techniques to verify include passive liveness (analysing natural facial movements), and active liveness (prompting the user to perform a task). Both of these user-friendly biometric verification methods help guard against sophisticated fraud attempts.
Is biometric verification GDPR compliant?
Yes, the best biometric identity verification should be fully GDPR compliant when biometric data is securely stored as encrypted digital templates. On consumer electronics, this means gaining explicit user consent, enforcing strict access controls, enabling data deletion or correction, and ensuring all processing is transparent and purpose-limited.
How does ComplyCube use biometric verification to enhance KYC?
ComplyCube integraties advanced biometric technologies into its Identity Verification (IDV) platform to streamline and secure the KYC process. The user-friendly platform combines various features such as passive/active liveness detection, AI-powered facial matching, spoofing, and deepfake detection for their biometric identity verification process. This allows businesses to verify identities through facial recognition, iris recognition, or voice recognition accurately within seconds. This reduces onboarding friction and meeting global compliance standards whether it be for bank accounts, patient identification, or border control. When used alongside document verification, registry checks, and real-time screening, biometric verification works. It helps organisations and clients achieve faster onboarding rates and higher fraud detection accuracy, across more than 220 countries and territories.